 1076
1076
 2024-03-27
2024-03-27
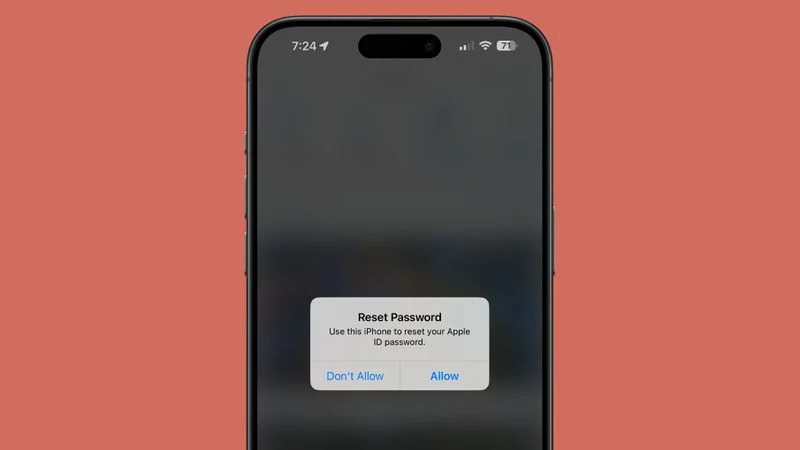
Phishing attacks taking advantage of what appears to be a bug in Apple's password reset feature have become increasingly common, according to a report from KrebsOnSecurity. Multiple Apple users have been targeted in an attack that bombards them with an endless stream of notifications or multi-factor authentication (MFA) messages in an attempt to get them to approve an Apple ID password change.
An attacker is able to cause the target's iPhone, Apple Watch, or Mac to display system-level password change approval texts over and over again, with the hope that the person being targeted will mistakenly approve the request or get tired of the notifications and click on the accept button. If the request is approved, the attacker is able to change the Apple ID password and lock the Apple user out of their account.
Because the password requests target the Apple ID, they pop up on all of a user's devices. The notifications render all linked Apple products unable to be used until the popups are dismissed one by one on each device. Twitter user Parth Patel recently shared his experience being targeted with the attack, and he says he could not use his devices until he clicked on "Don't Allow" for more than 100 notifications.
When attackers are unable to get the person to click "Allow" on the password change notification, targets often get phone calls that seem to be coming from Apple. On these calls, the attacker claims to know that the victim is under attack, and attempts to get the one-time password that is sent to a user's phone number when attempting a password change.
In Patel's case, the attacker was using information leaked from a people search website, which included name, current address, past address, and phone number, giving the person attempting to access his account ample information to work from. The attacker happened to have his name wrong, and he also became suspicious because he was asked for a one-time code that Apple explicitly sends with a message confirming that Apple does not ask for those codes.
The attack seems to hinge on the perpetrator having access to the email address and phone number associated with an Apple ID.
KrebsOnSecurity looked into the issue, and found that attackers appear to be using Apple's page for a forgotten Apple ID password. This page requires a user's Apple ID email or phone number, and it has a CAPTCHA. When an email address is put in, the page displays the last two digits of the phone number associated with the Apple account, and filing in the missing digits and hitting submit sends a system alert.
It is not clear how the attackers are abusing the system to send multiple messages to Apple users, but it appears to be a bug that is being exploited. It is unlikely that Apple's system is meant to be able to be used to send more than 100 requests, so presumably the rate limit is being bypassed.
Apple device owners targeted by this kind of attack should be sure to tap "Don't Allow" on all requests, and should be aware that Apple does not make phone calls requesting one-time password reset codes.
Source: Macrumors