 3612
3612
 2017-08-29
2017-08-29
Japanese cybersecurity company Trend Micro today announced its sixth annual Mobile Pwn2Own competition will be held at this year's PacSec security conference in Tokyo on Wednesday, November 1 and Thursday, November 2.

The competition is part of Trend Micro's Zero Day Initiative, a program for rewarding security researchers for responsibly disclosing vulnerabilities to companies like Apple, Google, Samsung, and Huawei.
This year, targeted devices include the iPhone 7, Samsung's Galaxy S8, Google's Pixel, and Huawei's Mate 9 Pro, each of which will be running the latest version of iOS or Android respectively with up-to-date security fixes.
Trend Micro is making more than $500,000 available to be won, with the cash prizes available varying by type of exploit. Mobile Safari exploits, for example, are worth up to $40,000, while an SMS-based vulnerability could net $60,000.
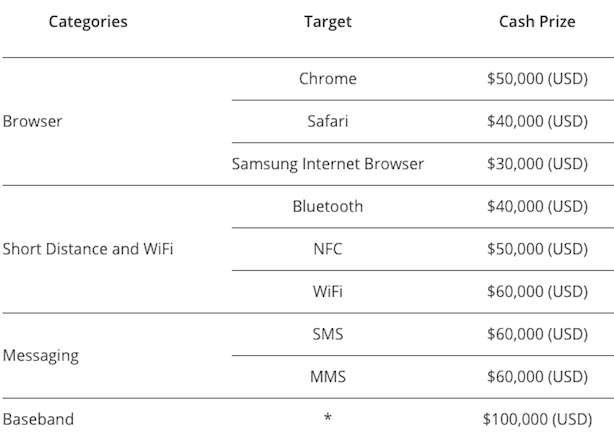
In addition to the standard categories and prizes, there are add-on bonuses of between $20,000 and $50,000 for executing code with kernel privileges and having a smartphone operating system's payload persist after a reboot.
Apple representatives have attended Pwn2Own competitions in the past, with all vulnerabilities made aware to them. Apple will have 90 days to produce patches for any iOS-related bugs before they are disclosed.
Earlier this year, at the 10th anniversary Pwn2Own competition, security researchers uncovered macOS Sierra vulnerabilities, including a Safari exploit which allowed them to scroll a message on a MacBook Pro's Touch Bar.
Source: macrumors