 3758
3758
 2017-03-17
2017-03-17
The seventeenth annual CanSecWest security conference is underway in downtown Vancouver, British Columbia, where researchers are competing in the 10th anniversary Pwn2Own computer hacking contest for over $1 million in prizes.
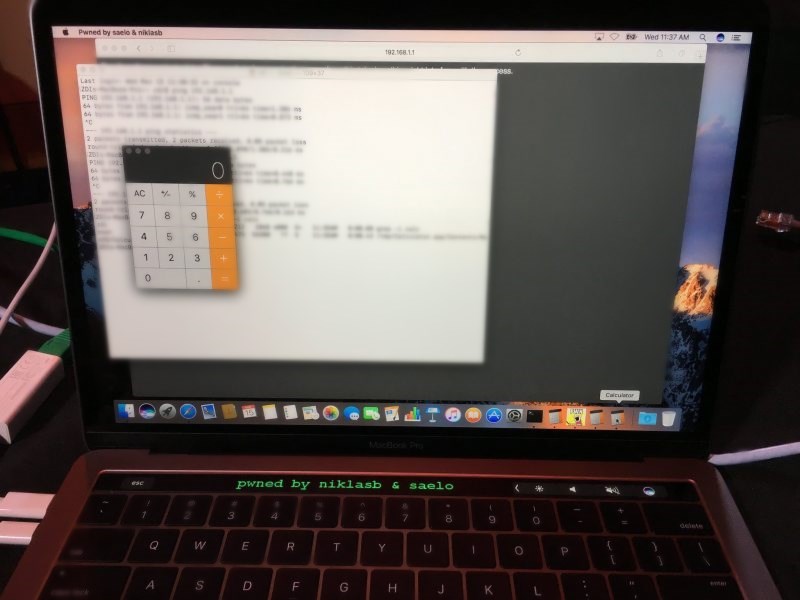
Day one results have already been published with a couple of successful Mac-related exploits already appearing in the list of achievements. Independent hackers Samuel Groß and Niklas Baumstark landed a partial success and earned $28,000 after targeting Safari with an escalation to root on macOS, which allowed them to scroll a message on a MacBook Pro Touch Bar.
In a partial win, Samuel Groß (@5aelo) and Niklas Baumstark (@_niklasb) earn some style points by leaving a special message on the touch bar of the Mac. They used a use-after-free (UAF) in Safari combined with three logic bugs and a null pointer dereference to exploit Safari and elevate to root in macOS. They still managed to earn $28,000 USD and 9 Master of Pwn points.
Later in the day, Chaitin Security Research Lab also targeted Safari with an escalation to root on macOS, finding success using a total of six bugs in their exploit chain, including "an info disclosure in Safari, four type confusion bugs in the browser, and a UAF in WindowServer". The combined efforts earned the team $35,000.
The participating teams earned a total of $233,000 in prizes on day one, including a leading $105,000 earned by Tencent Security, according to published details. Other software successfully targeted by contestants include Adobe Reader, Ubuntu Desktop, and Microsoft Edge on Windows.
Apple representatives have attended the Pwn2Own contest in the past, and affected parties are made aware of all security vulnerabilities discovered during the contest in order to patch them. Pwn2Own day two begins today at 8:30 a.m. Pacific and will involve additional exploit attempts against macOS and Safari.
Source: macrumors