 8694
8694
 2016-12-26
2016-12-26
Earlier this year,at the height of a very public battle between the FBI and Apple over whether the computer maker would help decrypt a mass murderer’s locked iPhone, it appeared that a little-known, 17-year-old Israeli firm named Cellebrite Mobile Synchronization might finally get its moment in the spotlight.

Cellebrite’s forensic tools include the Universal Forensic Extraction Device (UFED), hardware bundled with proprietary software that acquires, decodes, and analyzes data from smartphones, tablets, and portable GPS devices; the UFED4PC, which is standalone software for use on a PC; and the UFED Pro, an add-on to the UFED that does something called physical extraction, which siphons data directly from a phone’s flash memory chip. This can include deleted SMS messages and call histories as well as data collected by the phone and apps that the user is unaware is being collected.
Its new solution for extracting data from iPhone 5C’s running iOS 9 — the San Bernardino phone — can only be performed by a Cellebrite worker as part of the company’s Advanced Investigative Services division, also known as CAIS. This is a premium unlocking subscription service that costs $250,000 a year in the U.S., according to a DEA procurement record, and will also get customers help in bypassing encryption on the iPhone 4S and 5, the Samsung Galaxy S6 and Galaxy Note 5, and some Galaxy S7s, among other devices. Though Cellebrite will also unlock phones as a one-off service, for about $1,500 per phone.
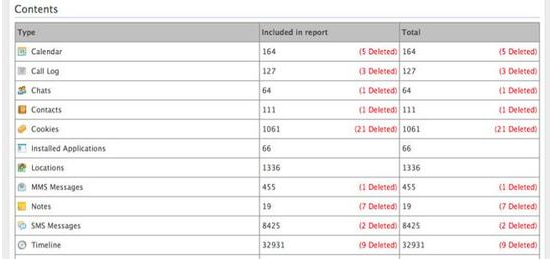
Bypassing encryption, the most vexing problem law enforcement faces today in mobile forensics, is one of Cellebrite’s biggest selling points. The company says it has been able to “crack the code to the screen locks” on a number of phone models, allowing it to access data on the phones without a password.
UFED can recover user's data even they deleted it already, Cellebrite's innovative UFED Pro Series is designed for the forensic examiners and investigators.
3uTools is wondering whether it can be used on iPhone 7 with iOS 10?